Title: Still life with oranges and stoneware dog
Creator: Paula Modersohn-Becker
Creator Lifespan: 1876/1907
Date: 1906/1907
Physical Dimensions: w90 x h65 cm
Provenance: Landesmuseum für Kunst und Kulturgeschichte Oldenburg
Type: Painting
CTF竞赛题目类型主要包含 Web 网络攻防 、 Reverse 逆向工程 、 Pwn 二进制漏洞利用 、 Crypto 密码攻击 、 Mobile 移动安全 以及 Misc 安全杂项 这六个类别。
本文为Crypto加解密方向。
赛题1
初始来源
#ISC2016# #phrackCTF# #easy RSA#
赛题传送门
【赛题类型】—>【CTF训练】
【比赛名称】—>【全部】
【题目类型】—>【Basic】
选择价值 50pt,类型为 Basic(本题也可为Crypto),名称为【easy RSA】的题目:
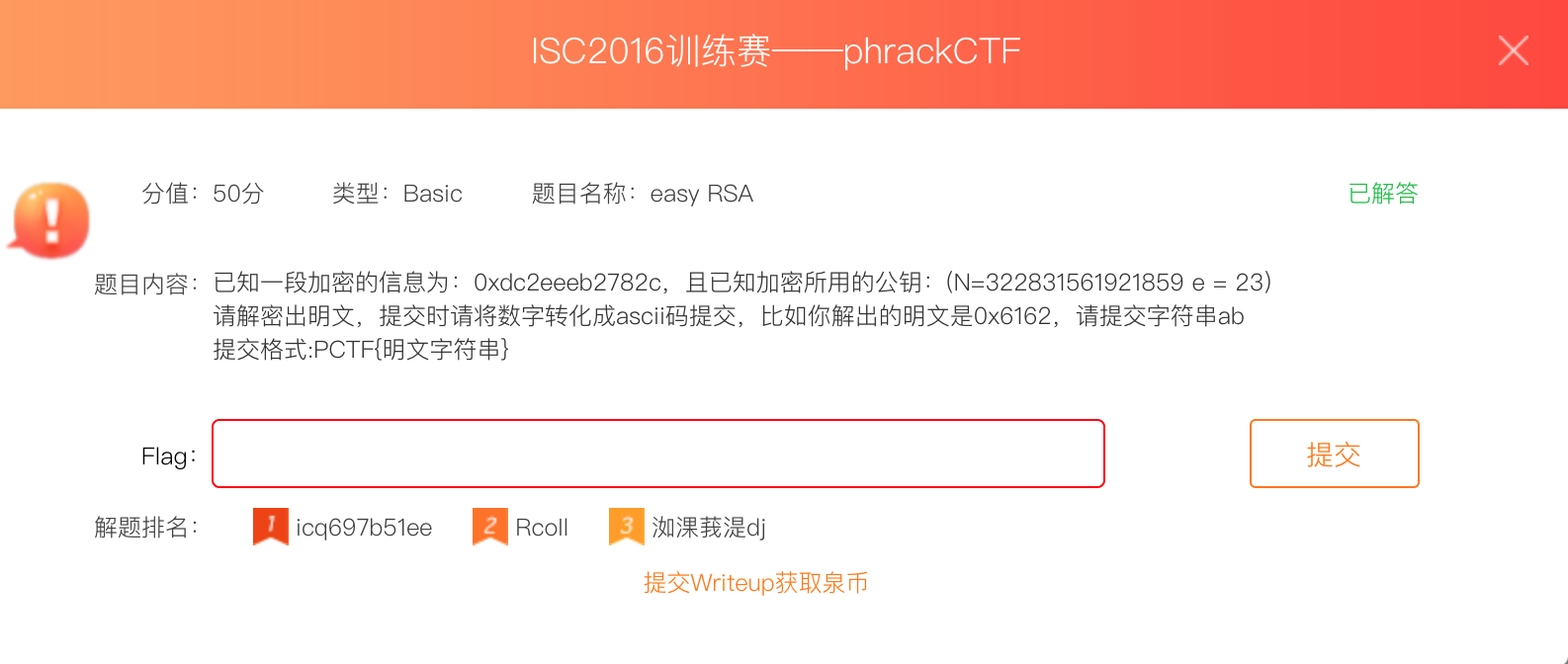
解题过程
题目内容为: 已知一段加密的信息为:0xdc2eeeb2782c,且已知加密所用的公钥:(N=322831561921859 e = 23)
请解密出明文,提交时请将数字转化成ascii码提交,比如你解出的明文是0x6162,请提交字符串ab
这里稍微解释一下RSA:
-
加密过程
选择两个大素数p和q,计算出模数N = p * q
计算φ = (p−1) * (q−1) 即N的欧拉函数,然后选择一个e (1<e<φ),且e和φ互质
取e的模反数为d,计算方法: e * d ≡ 1 (mod φ)
对明文A进行加密:
B≡A^e (mod n) 或 B = pow(A,e,n),得到的B即为密文对密文B进行解密,
A≡B^d( mod n) 或 A = pow(B,d,n),得到的A即为明文p 和 q :大整数N的两个因子(factor)
N:大整数N,我们称之为模数(modulus)
e 和 d:互为模反数的两个指数(exponent)
c 和 m:分别是密文和明文,这里一般指的是一个十进制的数
-
加密分析
RSA算法是一种非对称密码算法,所谓非对称,就是指该算法需要一对密钥,使用其中一个加密,则需要用另一个才能解密。
RSA的算法涉及三个参数,n、e、d。
其中,n是两个大质数p、q的积,n以二进制表示时所占用的位数,就是所谓的密钥长度。
e和d是一对相关的值,e可以任意取,但要求e与(p-1)(q-1)互质;再选择d,要求
(ed) ≡ 1(mod(p-1)×(q-1))。令φ = (p-1)(q-1) 上式即
d*e = 1 mod φ即:(d*e - 1)% φ = 0(n,e),(n,d)就是密钥对。其中(n,e)为公钥,(n,d)为私钥。RSA加解密的算法完全相同,设A为明文,B为密文,则:A≡B^d( mod n);B≡A^e (mod n);(公钥加密体制中,一般用公钥加密,私钥解密)
e和d可以互换使用,即:
A≡B^e (mod n);B≡A^d( mod n)
这里给了RSA中的N和e,思路就很清晰了,通过N和e求出public key,在通过公钥和密文可以求出明文
工具RsaCtfTool走起:
-
先来一波工具的参数介绍(具体可参考上述原址链接):、
-
通过题目给的N和e求出公钥:
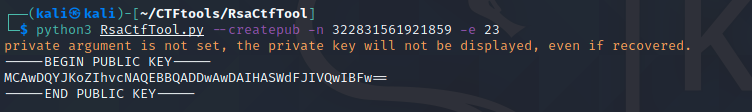
-
把公钥复制存放在文件./CTF/p.pem里
-
使用公钥和密文求出明文:
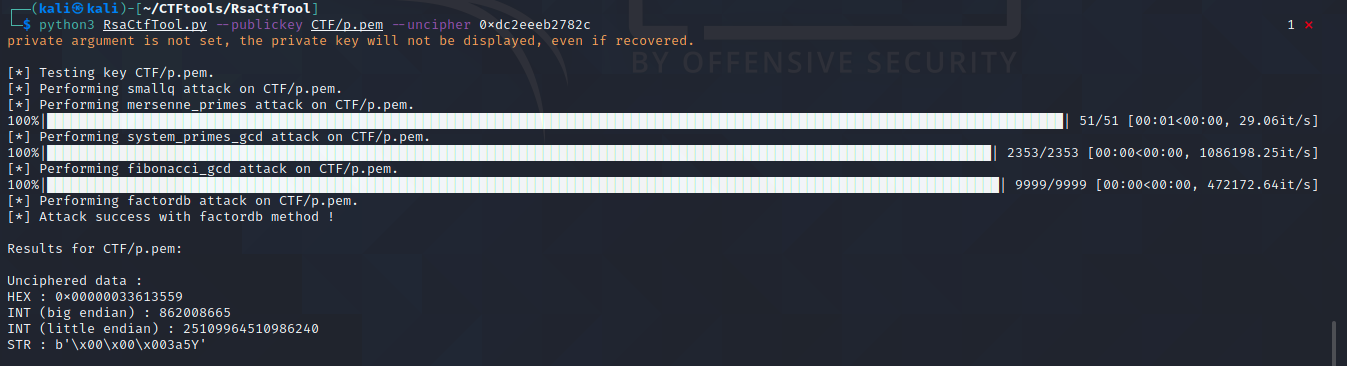
至此,得到flag。
赛题2
初始来源
#IceCTF# #RSA#
赛题传送门
【赛题类型】—>【CTF训练】
【比赛名称】—>【全部】
【题目类型】—>【Crypto】
选择价值50pt,类型为Crypto,名称为【RSA】的题目:
解题过程
题目内容为:
1
2
3
4
5
6
7
8
9
N=0x1564aade6f1b9f169dcc94c9787411984cd3878bcd6236c5ce00b4aad6ca7cb0ca8a0334d9fe0726f8b057c4412cfbff75967a91a370a1c1bd185212d46b581676cf750c05bbd349d3586e78b33477a9254f6155576573911d2356931b98fe4fec387da3e9680053e95a4709934289dc0bc5cdc2aa97ce62a6ca6ba25fca6ae38c0b9b55c16be0982b596ef929b7c71da3783c1f20557e4803de7d2a91b5a6e85df64249f48b4cf32aec01c12d3e88e014579982ecd046042af370045f09678c9029f8fc38ebaea564c29115e19c7030f245ebb2130cbf9dc1c340e2cf17a625376ca52ad8163cfb2e33b6ecaf55353bc1ff19f8f4dc7551dc5ba36235af9758b
e=0x10001
phi=0x1564aade6f1b9f169dcc94c9787411984cd3878bcd6236c5ce00b4aad6ca7cb0ca8a0334d9fe0726f8b057c4412cfbff75967a91a370a1c1bd185212d46b581676cf750c05bbd349d3586e78b33477a9254f6155576573911d2356931b98fe4fec387da3e9680053e95a4709934289dc0bc5cdc2aa97ce62a6ca6ba25fca6ae366e86eed95d330ffad22705d24e20f9806ce501dda9768d860c8da465370fc70757227e729b9171b9402ead8275bf55d42000d51e16133fec3ba7393b1ced5024ab3e86b79b95ad061828861ebb71d35309559a179c6be8697f8a4f314c9e94c37cbbb46cef5879131958333897532fea4c4ecd24234d4260f54c4e37cb2db1a0
d=0x12314d6d6327261ee18a7c6ce8562c304c05069bc8c8e0b34e0023a3b48cf5849278d3493aa86004b02fa6336b098a3330180b9b9655cdf927896b22402a18fae186828efac14368e0a5af2c4d992cb956d52e7c9899d9b16a0a07318aa28c8202ebf74c50ccf49a6733327dde111393611f915f1e1b82933a2ba164aff93ef4ab2ab64aacc2b0447d437032858f089bcc0ddeebc45c45f8dc357209a423cd49055752bfae278c93134777d6e181be22d4619ef226abb6bfcc4adec696cac131f5bd10c574fa3f543dd7f78aee1d0665992f28cdbcf55a48b32beb7a1c0fa8a9fc38f0c5c271e21b83031653d96d25348f8237b28642ceb69f0b0374413308481
c=0x126c24e146ae36d203bef21fcd88fdeefff50375434f64052c5473ed2d5d2e7ac376707d76601840c6aa9af27df6845733b9e53982a8f8119c455c9c3d5df1488721194a8392b8a97ce6e783e4ca3b715918041465bb2132a1d22f5ae29dd2526093aa505fcb689d8df5780fa1748ea4d632caed82ca923758eb60c3947d2261c17f3a19d276c2054b6bf87dcd0c46acf79bff2947e1294a6131a7d8c786bed4a1c0b92a4dd457e54df577fb625ee394ea92b992a2c22e3603bf4568b53cceb451e5daca52c4e7bea7f20dd9075ccfd0af97f931c0703ba8d1a7e00bb010437bb4397ae802750875ae19297a7d8e1a0a367a2d6d9dd03a47d404b36d7defe8469
这题目直接啥参数都给了,套用题目1中的科普公式:
对密文B进行解密,A≡B^d( mod n) 或 A = pow(B,d,n),得到的A即为明文。
1
2
3
4
5
6
7
8
import libnum
N=0x1564aade6f1b9f169dcc94c9787411984cd3878bcd6236c5ce00b4aad6ca7cb0ca8a0334d9fe0726f8b057c4412cfbff75967a91a370a1c1bd185212d46b581676cf750c05bbd349d3586e78b33477a9254f6155576573911d2356931b98fe4fec387da3e9680053e95a4709934289dc0bc5cdc2aa97ce62a6ca6ba25fca6ae38c0b9b55c16be0982b596ef929b7c71da3783c1f20557e4803de7d2a91b5a6e85df64249f48b4cf32aec01c12d3e88e014579982ecd046042af370045f09678c9029f8fc38ebaea564c29115e19c7030f245ebb2130cbf9dc1c340e2cf17a625376ca52ad8163cfb2e33b6ecaf55353bc1ff19f8f4dc7551dc5ba36235af9758b
d=0x12314d6d6327261ee18a7c6ce8562c304c05069bc8c8e0b34e0023a3b48cf5849278d3493aa86004b02fa6336b098a3330180b9b9655cdf927896b22402a18fae186828efac14368e0a5af2c4d992cb956d52e7c9899d9b16a0a07318aa28c8202ebf74c50ccf49a6733327dde111393611f915f1e1b82933a2ba164aff93ef4ab2ab64aacc2b0447d437032858f089bcc0ddeebc45c45f8dc357209a423cd49055752bfae278c93134777d6e181be22d4619ef226abb6bfcc4adec696cac131f5bd10c574fa3f543dd7f78aee1d0665992f28cdbcf55a48b32beb7a1c0fa8a9fc38f0c5c271e21b83031653d96d25348f8237b28642ceb69f0b0374413308481
c=0x126c24e146ae36d203bef21fcd88fdeefff50375434f64052c5473ed2d5d2e7ac376707d76601840c6aa9af27df6845733b9e53982a8f8119c455c9c3d5df1488721194a8392b8a97ce6e783e4ca3b715918041465bb2132a1d22f5ae29dd2526093aa505fcb689d8df5780fa1748ea4d632caed82ca923758eb60c3947d2261c17f3a19d276c2054b6bf87dcd0c46acf79bff2947e1294a6131a7d8c786bed4a1c0b92a4dd457e54df577fb625ee394ea92b992a2c22e3603bf4568b53cceb451e5daca52c4e7bea7f20dd9075ccfd0af97f931c0703ba8d1a7e00bb010437bb4397ae802750875ae19297a7d8e1a0a367a2d6d9dd03a47d404b36d7defe8469
m = libnum.n2s(pow(c, d, N))
print(m)
运行即可:
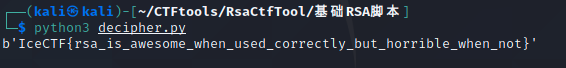
至此,得到flag。
赛题3
初始来源
#2017第二届广东省强网杯线上赛# #RSA#
赛题传送门
【赛题类型】—>【CTF训练】
【比赛名称】—>【全部】
【题目类型】—>【Crypto】
选择价值50pt,类型为Crypto,名称为【RSA】的题目:
解题过程
题目内容为:
1
2
3
n is 966808932627497190635859236054960349099463975227350564265384373280336699853387254070662881265937565163000758606154308757944030571837175048514574473061401566330836334647176655282619268592560172726526643074499534129878217409046045533656897050117438496357231575999185527675071002803951800635220029015932007465117818739948903750200830856115668691007706836952244842719419452946259275251773298338162389930518838272704908887016474007051397194588396039111216708866214614779627566959335170676055025850932631053641576566165694121420546081043285806783239296799795655191121966377590175780618944910532816988143056757054052679968538901460893571204904394975714081055455240523895653305315517745729334114549756695334171142876080477105070409544777981602152762154610738540163796164295222810243309051503090866674634440359226192530724635477051576515179864461174911975667162597286769079380660782647952944808596310476973939156187472076952935728249061137481887589103973591082872988641958270285169650803792395556363304056290077801453980822097583574309682935697260204862756923865556397686696854239564541407185709940107806536773160263764483443859425726953142964148216209968437587044617613518058779287167853349364533716458676066734216877566181514607693882375533
e is 65537
c is 168502910088858295634315070244377409556567637139736308082186369003227771936407321783557795624279162162305200436446903976385948677897665466290852769877562167487142385308027341639816401055081820497002018908896202860342391029082581621987305533097386652183849657065952062433988387640990383623264405525144003500286531262674315900537001845043225363148359766771033899680111076181672797077410584747509581932045540801777738548872747597899965366950827505529432483779821158152928899947837196391555666165486441878183288008753561108995715961920472927844877569855940505148843530998878113722830427807926679324241141182238903567682042410145345551889442158895157875798990903715105782682083886461661307063583447696168828687126956147955886493383805513557604179029050981678755054945607866353195793654108403939242723861651919152369923904002966873994811826391080318146260416978499377182540684409790357257490816203138499369634490897553227763563553981246891677613446390134477832143175248992161641698011195968792105201847976082322786623390242470226740685822218140263182024226228692159380557661591633072091945077334191987860262448385123599459647228562137369178069072804498049463136233856337817385977990145571042231795332995523988174895432819872832170029690848
这里给了n、e、c,和题目1一样的条件。
先按题目1的方法走了一遍:
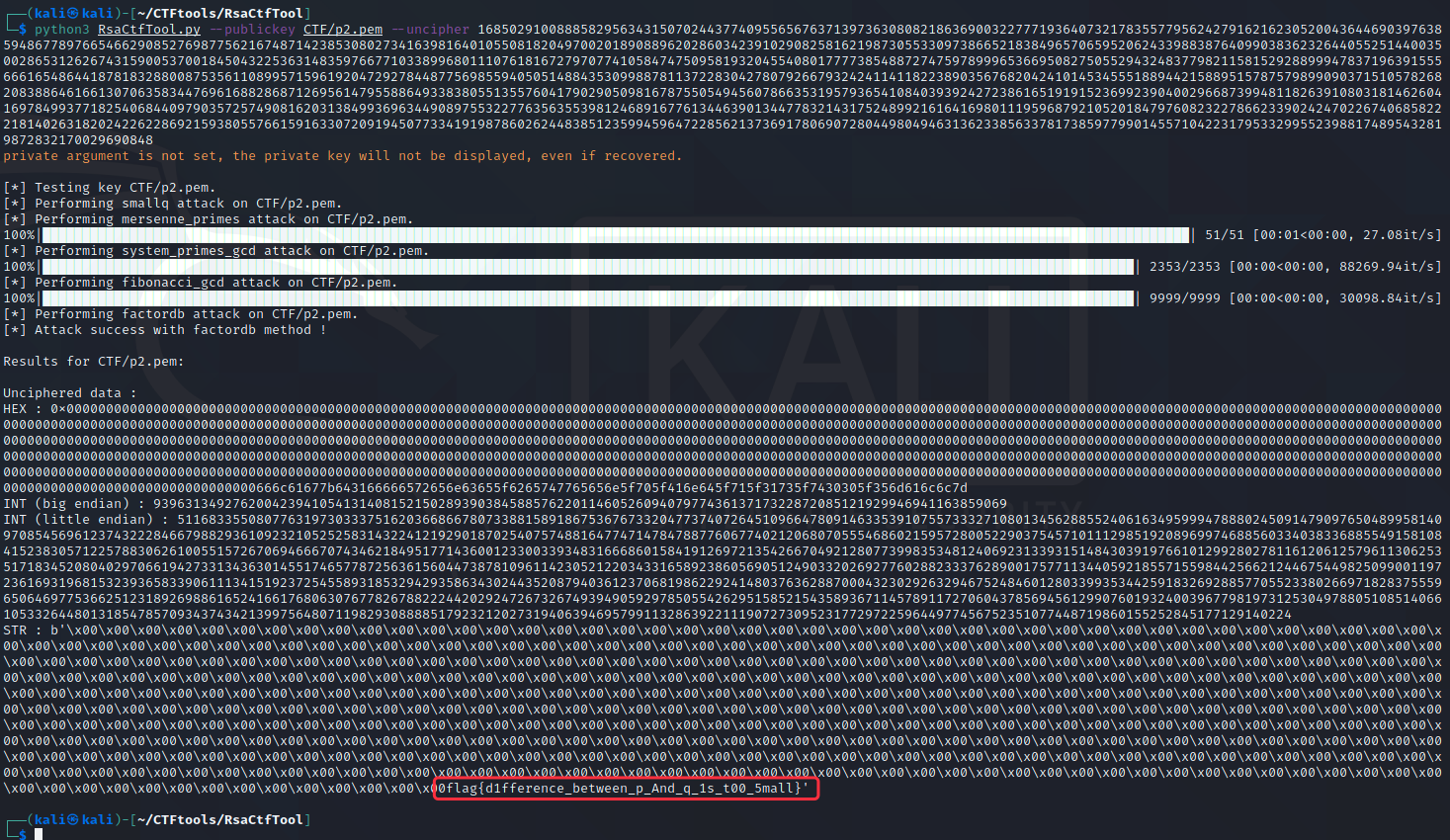
至此,得到flag。
总结
后面还有好几个题目都是RSA的,基本上快速的解法主要还是使用这套工具。但是熟知原理也很重要,建议多去网上搜一下,吃透原理,再使用工具会更得心应手。